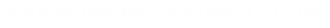Electronic commerce has appeared, largely because of the intervention of financial institutions making electronic payments between parties. These institutions have played the role of trusted third parties, who attest to the declarations of will that form part of their contracts, assigning them a time and date and thereby allowing payment to happen. Facing this model, and based on trust, a system based on cryptographic evidence has emerged.

Bitcoin is a peer-to-peer electronic money system that allows payment directly, without the intervention of a trusted third party. Likewise, Bitcoin could be defined as a chain of digital signatures, and specifically, through the verification of the latter, we can verify the transaction history and, therefore the chain of digital signatures, and therefore who it belongs to (the chain of ownership). Notwithstanding the above, the inherent problem of double-spending still exists. However, the solution comes from the "peer-to-peer" network, which solves forks in the chain of blocks (Blockchain) and possible fraud.
Any electronic currency is effectively a chain of digital signatures. Each owner digitally signs the private key with the cryptographic hash of the previous transaction and the public key of the beneficiary and, through the latter, the owner checks their digital signature.
Source: "Bitcoin: A Peer-to-Peer Electronic Cash System". Satoshi Nakamoto
The peer-to-peer e-money system necessarily requires the use of so-called public key infrastructure (PKI) to configure itself as a secure platform. the infrastructure of this key, according to Alex and Don Tapscott (1), "is an advanced form of asymmetric cryptography so that users have two keys that do not perform the same function: one is to encrypt and the other to decrypt. Hence they are asymmetrical".
To surmount the aforementioned security problem inherent in the Bitcoin system consisting of spending twice, two alternatives in principle would work: either the intervention of a central authority, a trusted third party, to verify each of the transactions carried out; or the use of a time stamp server. By virtue of this, each transaction is tagged with a time stamp using a cryptographic hash, and is publicly announced.
To surmount the security problem, two alternatives in principle would work: either a trusted third party, to verify each of the transactions carried out, or the use of a time stamp server
Each stamp includes the previous one, assembling a string and, therefore, determining a single order of transactions. Consequently, it is unlikely that there could be double expenditure by carrying out, at the same time, different transactions with different beneficiaries.
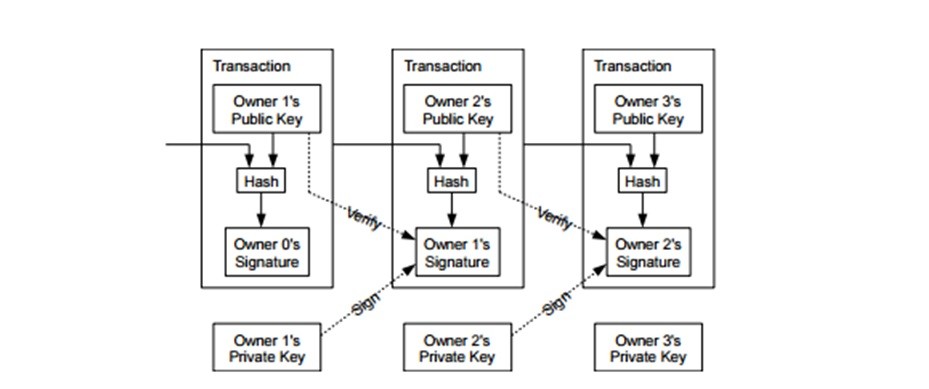
Also, the so-called proof-of-work, a system similar to Adam Hashcash, allows you to implement time stamp in the peer-to-peer electronic money system. In fact, through the proof-of-work, the transactions made are already verified and included in blocks in chronological order, configuring a real chain of blocks (Blockchain). Effectively, from a previous hash, a correct "nonce" (pseudo-random number which can be used only once) is added to the block.
Source: "Bitcoin: A Peer-to-Peer Electronic Cash System". Satoshi Nakamoto
Once reached this point, the block cannot be changed without redoing the previous calculation work. However, as the work test depends on the immediately preceding block, to modify a past one, we will need to rework the test of the block and all previous ones, and, if it were not enough, to reach and advance the work of the so-called honest computing nodes. Consequently, the difficulty of corrupting the block chain increases exponentially. In fact, in the case of forks in this chain, the decision of most nodes in the peer-to-peer system is represented by the term "longest chain", the most effort expended, and this majority of nodes will continue the proof-of-work test using this one and never on unwanted, shorter forks.
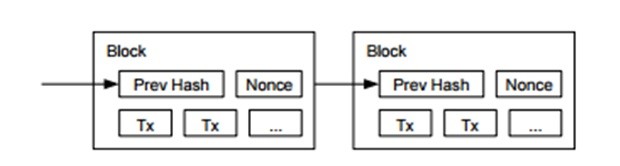
Source: blockchain.info.
Fundamentally, the security of the Bitcoin system depends on the CPU power of the honest nodes against possible attacks of other groups of nodes. In this sense, Alex and Don Tapscott (2) pronounce: "the longest chain is usually the safest. the relative antiquity of Satoshi's Blockchain and its already established base of Bitcoins users and miners increases its security. Attacking it would require more processing power than attacking short chains."
The feared "fifty-one percent attack", together with quantum computing, are currently the main threats to Bitcoin's security. Dirk Haubrich (Head of Consumer Protection, Financial Innovation and Payments) of the European Banking Authority (EBA) warns that Bitcoin's biggest problem remains the threat of a 51% attack (3). Likewise, Bitcoin is vulnerable to quantum computing. In fact, the United States National Security Agency (NSA), for example, has the potential to break Bitcoin's cryptography through its quantum computers (4).
In another sense, the security vulnerability of Bitcoin is generally due to the responsibility of keeping keys secure and, consequently, due to failures attributable to users. Also, the theft of wallets poses a serious threat to its users.
The security vulnerability of Bitcoin is generally due to the responsibility of keeping the keys safe
In conclusion, the security measures are integrated into the "peer-to-peer" electronic payment system, based on "Blockchain". The network effect of Bitcoin, the user base of the network, increases system security as the block chain grows. As long as most of the processing power (51%) is under the control of honest users, the Bitcoin network will be secure.
(1)y (2) Alex y Don Tapscott, Blockchain's revolution, Deusto, 2017.
(3)Emily Spaven, EBA: 51% Attack Remains Bitcoin’s Biggest Problem, coindesk.com, 2015.
(4) Andreas Antonopoulos, Proof of beats. Quantum Badger. Sound cloud. com, 2017.